- Out-of-Stock
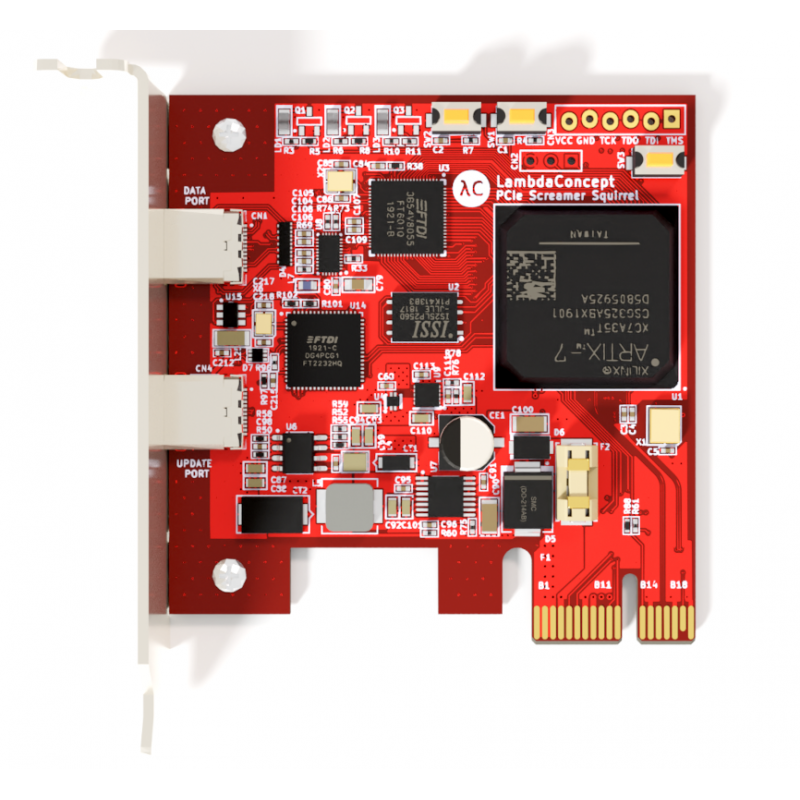





Screamer PCIe Squirrel with a Low-Profile form factor and PCIe x1 connectivity designed for DMA (Direct Memory Access) attacks over PCI Express.
The board is officially supported by PCILeech and comes pre-flashed with PCILeech FPGA gateware.
Our JtagSerial cable is no longer needed for gateware updates, just connect through the USB update port !
The web shop price is tax excluded, expect to pay the value-added tax (usually 20%) or any other extra fees at the reception of the package in your destination country, including when shipping to France or Europe (All packages are shipped from Hong Kong).
http://docs.lambdaconcept.com/screamer/index.html
PCIe is the main high speed way of communicating between a processor and its peripherals. It is used in PC (also encapsulated in Thunderbolt) and now even in mobile phones. Doing security research on a PCIe system is complex because it requires expensive tools that are not that common when packet generation is needed. Screamer provides a such tool at a reasonable price.
https://github.com/ufrisk/pcileech
https://github.com/ufrisk/pcileech-fpga